

XOR Cipher
A symmetric key encryption cipher that is simple yet powerful.
What is the XOR cipher?
The XOR cipher is a simple encryption algorithm that uses the XOR (exclusive or) operator. In this cipher, a key is used to perform the XOR operation on each character of the plaintext to produce the corresponding character of the ciphertext.
Plain Text
Key
Cipher Text
How does the XOR cipher work?
The XOR cipher is a type of encryption algorithm that uses the XOR (exclusive or) operation to encrypt plaintext into ciphertext. In this cipher, a key, which is also a binary string, is used to perform the XOR operation on each bit of the plaintext to produce the corresponding bit of the ciphertext.
The XOR operation takes two input bits and outputs a single bit, which is 1 if the two input bits are different, and 0 if they are the same. When the XOR operation is applied to the plaintext and the key, the resulting binary string is the ciphertext.
To decrypt the ciphertext, the same key is used to perform the XOR operation on each bit of the ciphertext to recover the original plaintext message. The strength of the XOR cipher depends on the strength and randomness of the key used. If the key is too short or predictable, the ciphertext can be easily decrypted through brute force or other methods.
Therefore, the XOR cipher is not considered a secure encryption algorithm for modern cryptographic applications, and more advanced algorithms such as AES and RSA are typically used instead. However, the XOR cipher is still used in some applications where simplicity and speed are more important than security.
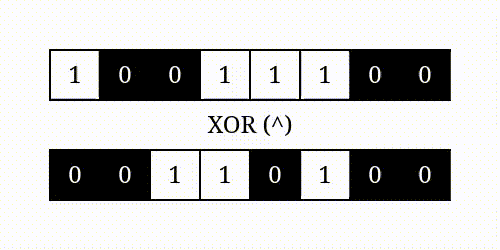
Visualizing the XOR cipher
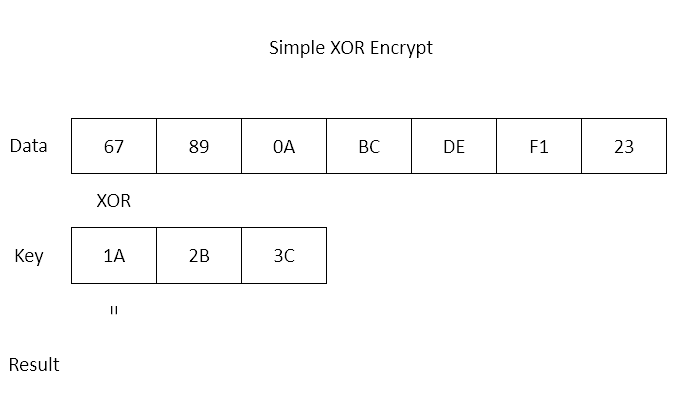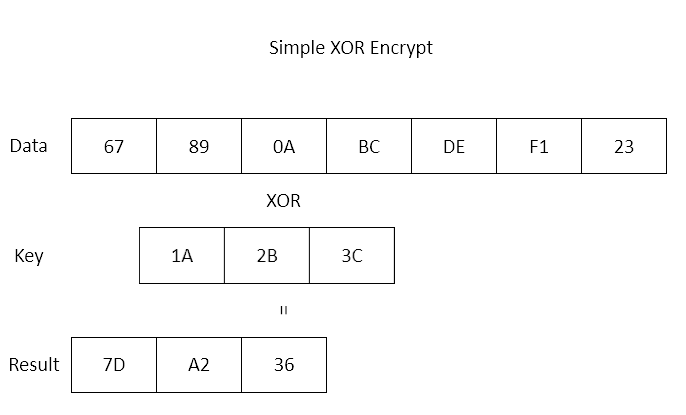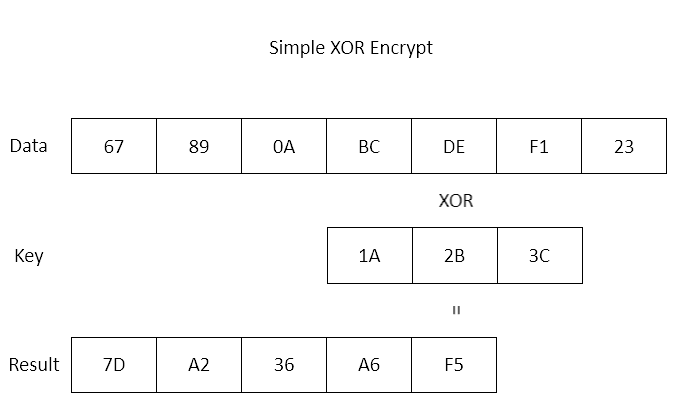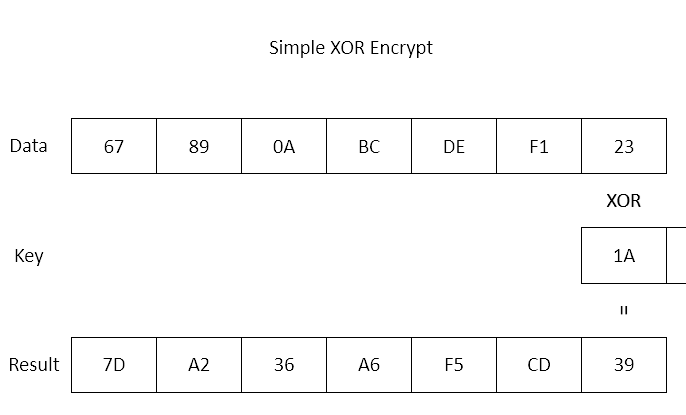
History
The XOR cipher, also known as the Vernam cipher, is a type of encryption that was invented in 1917 by Gilbert Vernam, an American telegraph engineer. Vernam's original invention used a paper tape that was punched with a random sequence of holes, which were used as the key for the encryption process.
The XOR cipher was initially used for telegraphy and later for teletype systems. During World War II, the cipher was used by the United States for secure communications, particularly for messages transmitted over the transatlantic cable.
In the 1950s and 1960s, the XOR cipher was used for computer encryption, particularly for military and diplomatic communications. However, the cipher was eventually found to be vulnerable to certain types of attacks, such as known plaintext attacks, where an attacker has access to both the encrypted message and the original message.
Despite its vulnerabilities, the XOR cipher remains an important part of cryptography history and continues to be used in certain contexts, particularly as a component of more complex encryption algorithms.
